Data breaches are a growing concern for businesses and individuals alike. “Timeline of Events: From Breach to Settlement Payout” delves into the complex journey organizations navigate after a data breach, from initial detection to the final settlement payout. This journey encompasses a range of critical steps, each with its own challenges and considerations.
From the initial detection of a breach to the final settlement payout, this comprehensive guide explores the key phases and considerations involved in responding to a data breach. It provides insights into the legal requirements, security protocols, and negotiation strategies that shape the entire process.
Contents List
Initial Breach Detection
Data breaches are a significant threat to organizations of all sizes, and the ability to detect a breach early is crucial for minimizing damage and mitigating risks. Organizations employ various methods to identify potential breaches, including:
Methods for Detecting Data Breaches

- Security Information and Event Management (SIEM) Systems:These systems collect and analyze security data from various sources, such as firewalls, intrusion detection systems, and servers, to identify suspicious activities and potential breaches. SIEM systems can detect anomalies, unusual patterns, and unauthorized access attempts, providing early warning signals.
- Intrusion Detection Systems (IDS):IDS are software or hardware devices that monitor network traffic for malicious activity. They can detect network scans, unauthorized access attempts, and known attack signatures. IDS can trigger alerts and provide real-time information about potential threats.
- Vulnerability Scanning:Regular vulnerability scans help identify weaknesses in systems and applications that could be exploited by attackers. These scans assess the security posture of an organization’s infrastructure and identify potential vulnerabilities that need to be addressed.
- Endpoint Security Solutions:Endpoint security software protects individual computers and devices from malware and other threats. These solutions can monitor file activity, detect suspicious behavior, and prevent unauthorized access to sensitive data.
- Log Analysis:Regular analysis of system logs, including security logs, application logs, and network logs, can reveal suspicious activity and potential breaches. Log analysis can identify unauthorized access attempts, data exfiltration attempts, and other security events.
- Employee Reporting:Organizations encourage employees to report any suspicious activity or unusual events they encounter. This can include unusual emails, unexpected requests for access, or unusual system behavior.
Immediate Actions Upon Breach Discovery
Once a data breach is suspected, organizations must act swiftly and decisively to contain the damage and mitigate the impact. The following actions are typically taken:
- Isolate the Affected Systems:Disconnect the compromised systems from the network to prevent further spread of the breach and limit the attacker’s access to sensitive data. This involves isolating affected servers, workstations, or network segments.
- Secure the Breach:Take immediate steps to close the security gap that allowed the breach to occur. This might involve patching vulnerabilities, changing passwords, and implementing additional security controls.
- Initiate Incident Response:Activate the organization’s incident response plan, which Artikels the steps to be taken in the event of a data breach. This involves assembling the incident response team, communicating with key stakeholders, and coordinating the response effort.
- Gather Evidence:Collect and preserve evidence of the breach, including system logs, network traffic data, and forensic artifacts. This evidence will be crucial for investigating the breach, determining the scope of the damage, and potentially pursuing legal action.
- Notify Relevant Parties:Inform key stakeholders, including senior management, legal counsel, and regulatory authorities, about the breach. This ensures that everyone is aware of the situation and can take appropriate action.
Challenges in Initial Breach Response
The initial stages of breach response can be challenging, and organizations face various hurdles:
- Identifying the Breach:Detecting a data breach can be difficult, especially for sophisticated attacks that can go undetected for extended periods. The attacker may use stealthy techniques to evade detection, making it challenging to identify the breach in its early stages.
- Determining the Scope:Once a breach is identified, determining the extent of the compromise can be challenging. The attacker may have accessed various systems and data, and it may take time to assess the full impact of the breach.
- Limited Resources:Organizations may have limited resources available to respond to a data breach effectively. This can include insufficient staff, inadequate security tools, or limited budget for incident response activities.
- Time Constraints:Responding to a data breach requires swift action. Delays in identifying the breach, containing the damage, and notifying relevant parties can significantly increase the risk of further harm and legal repercussions.
- Lack of Experience:Some organizations may lack the experience and expertise to handle a data breach effectively. This can lead to mistakes, delays, and increased risk.
Incident Response and Containment
Once a data breach is detected, organizations must act swiftly to contain the damage and prevent further exploitation. This involves a comprehensive incident response process, which includes several key steps.
Steps Involved in Containment
- Isolate the Affected Systems:Disconnecting compromised systems from the network is crucial to prevent the spread of malware and unauthorized access to sensitive data. This involves isolating affected servers, workstations, or network segments.
- Secure the Breach:Patching vulnerabilities, changing passwords, and implementing additional security controls are essential to close the security gap that allowed the breach to occur. This helps prevent further exploitation by the attacker.
- Gather Evidence:Collect and preserve evidence of the breach, including system logs, network traffic data, and forensic artifacts. This evidence will be crucial for investigating the breach, determining the scope of the damage, and potentially pursuing legal action.
- Monitor for Further Activity:Continuously monitor the network and systems for any signs of further malicious activity. This includes checking for new malware infections, unauthorized access attempts, and data exfiltration attempts.
- Communicate with Stakeholders:Keep key stakeholders, including senior management, legal counsel, and regulatory authorities, informed about the breach and the response efforts. This ensures that everyone is aware of the situation and can take appropriate action.
Role of Security Teams and External Experts
Security teams play a critical role in incident response, working to contain the breach, gather evidence, and restore affected systems. External experts, such as cybersecurity consultants and forensic investigators, can provide specialized skills and resources to assist in the response effort.
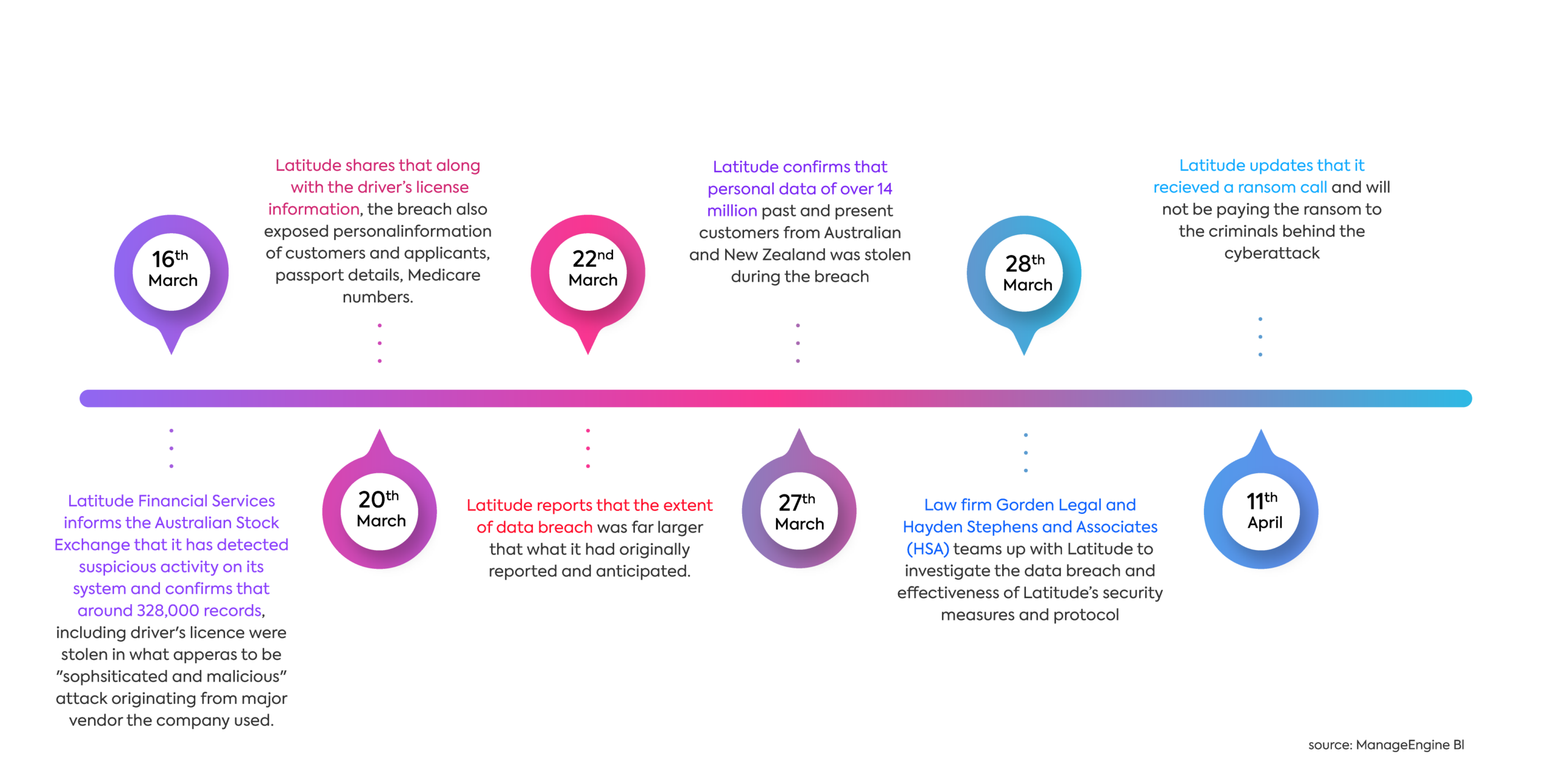
Timeline of Key Activities, Timeline of Events: From Breach to Settlement Payout
- Initial Detection (0-24 hours):This stage involves identifying the breach, isolating affected systems, and securing the breach. The focus is on minimizing damage and preventing further exploitation.
- Investigation and Evidence Gathering (24-72 hours):During this phase, the incident response team conducts a thorough investigation to determine the scope of the breach, identify the attacker’s methods, and gather evidence for future analysis and legal action.
- Containment and Remediation (72-168 hours):This stage involves implementing remediation measures, such as patching vulnerabilities, restoring compromised systems, and enhancing security controls. The goal is to restore normal operations and prevent future breaches.
- Post-Incident Review and Analysis (Ongoing):After the initial response, organizations conduct a post-incident review to analyze the breach, identify lessons learned, and implement improvements to their security posture. This continuous improvement process helps prevent future breaches.
Data Breach Notification
Data breach notification laws require organizations to notify individuals whose personal information has been compromised. These laws vary by jurisdiction, but they generally require organizations to take specific steps to inform affected individuals and relevant authorities.
Legal Requirements for Data Breach Notification
- Notification Timelines:Most data breach notification laws specify a timeframe within which organizations must notify affected individuals. This timeframe can range from 30 to 60 days after the breach is discovered.
- Content of Notification:The notification must include specific information about the breach, such as the date of the breach, the type of information compromised, and the steps individuals can take to protect themselves. The notification should also include contact information for the organization and relevant authorities.
- Methods of Notification:Organizations can use various methods to notify affected individuals, including email, postal mail, or telephone calls. The method of notification should be appropriate for the situation and should reach the individuals effectively.
- Reporting to Authorities:Many jurisdictions require organizations to report data breaches to relevant authorities, such as data protection agencies or law enforcement. These reporting requirements vary by jurisdiction.
Process of Notifying Affected Individuals and Authorities
- Identify Affected Individuals:The first step is to identify all individuals whose personal information has been compromised. This may involve reviewing databases, logs, and other records to determine the scope of the breach.
- Develop a Notification Plan:Organizations should develop a plan for notifying affected individuals, including the method of notification, the content of the notification, and the timeframe for notification. This plan should comply with all applicable laws and regulations.
- Prepare Notification Materials:Prepare the notification materials, including the letter or email that will be sent to affected individuals. The notification should be clear, concise, and easy to understand. It should also provide practical advice for individuals to protect themselves.
- Deliver Notifications:Send the notifications to affected individuals using the chosen method, such as email, postal mail, or telephone calls. Organizations should track the delivery of notifications and maintain records of the notification process.
- Report to Authorities:If required by law, organizations should report the breach to relevant authorities, such as data protection agencies or law enforcement. The reporting process and the information required will vary by jurisdiction.
Examples of Breach Notification Templates and Communication Strategies
- Breach Notification Letter:A formal letter outlining the details of the breach, the type of information compromised, the steps taken to mitigate the impact, and the advice for individuals to protect themselves.
- Breach Notification Email:An email message containing the same information as the letter, but in a more concise format. The email should also include a link to a website with more detailed information about the breach.
- Phone Call Notification:A phone call to inform individuals about the breach, but this method may not be practical for large-scale breaches. The phone call should provide a brief overview of the breach and direct individuals to a website for more detailed information.
- Website Announcement:An announcement on the organization’s website, providing details about the breach and resources for affected individuals. This method can be used to reach a large audience quickly and efficiently.
Investigation and Forensic Analysis
After a data breach is detected, a thorough investigation is essential to determine the scope and impact of the breach. This investigation involves forensic analysis to identify the source of the breach, the data compromised, and the attacker’s methods.
Process of Conducting a Thorough Investigation
- Establish a Chain of Custody:Preserve the integrity of evidence by establishing a chain of custody. This involves documenting the handling and storage of evidence from the time it is collected to the time it is presented in court or during an investigation.
- Secure the Crime Scene:Secure the affected systems and network to prevent further data loss or tampering with evidence. This may involve isolating affected systems, disconnecting them from the network, and preventing unauthorized access.
- Gather Evidence:Collect relevant evidence, including system logs, network traffic data, forensic artifacts, and any other information that can help determine the scope of the breach and the attacker’s methods. This evidence will be crucial for the investigation.
- Analyze Evidence:Analyze the collected evidence to identify the source of the breach, the data compromised, and the attacker’s methods. This may involve using specialized forensic tools and techniques to examine system logs, network traffic data, and other evidence.
- Document the Investigation:Document the entire investigation process, including the steps taken, the evidence collected, the analysis performed, and the conclusions drawn. This documentation will be essential for reporting the breach, pursuing legal action, and improving security measures.
Role of Forensic Analysis in Identifying the Source and Data Compromised
Forensic analysis plays a crucial role in identifying the source of the breach and the data compromised. Forensic experts use specialized tools and techniques to examine system logs, network traffic data, and other evidence to identify the attacker’s methods, the entry point of the breach, and the data that was accessed or exfiltrated.
Best Practices for Documenting the Investigation and Evidence Gathering
- Detailed Documentation:Create detailed documentation of the investigation, including the steps taken, the evidence collected, the analysis performed, and the conclusions drawn. This documentation should be comprehensive and accurate, providing a complete record of the investigation process.
- Chain of Custody:Maintain a strict chain of custody for all evidence collected. This involves documenting the handling and storage of evidence from the time it is collected to the time it is presented in court or during an investigation. This ensures that the evidence is not tampered with and maintains its integrity.
- Secure Storage:Store all evidence securely to prevent unauthorized access or tampering. This may involve using secure storage facilities, encrypting evidence, and implementing access controls to restrict access to authorized personnel.
- Timely Documentation:Document the investigation as it progresses, including the date and time of each step, the individuals involved, and the actions taken. This ensures that the documentation is accurate and up-to-date.
- Digital Evidence:If digital evidence is collected, ensure that it is properly preserved and authenticated. This may involve using specialized forensic tools to create images of hard drives, memory dumps, and other digital evidence.
Remediation and Recovery: Timeline Of Events: From Breach To Settlement Payout
After a data breach, organizations must take steps to restore compromised systems and data, enhance security measures, and prevent future breaches. This process involves several key activities.
Steps Involved in Restoring Compromised Systems and Data
- System Recovery:Restore compromised systems to their previous state, including reinstalling operating systems, restoring data from backups, and patching vulnerabilities. This process may involve using system recovery tools, data backup solutions, and security patches.
- Data Recovery:Recover any data that was lost or compromised during the breach. This may involve using data recovery tools, restoring data from backups, or contacting data recovery specialists. The effectiveness of data recovery depends on the type of data lost and the availability of backups.
- System Hardening:Implement security measures to harden systems and prevent future breaches. This may involve configuring firewalls, implementing intrusion detection systems, and using security software to protect against malware and other threats.
- Password Reset:Reset passwords for all affected accounts, including user accounts, administrative accounts, and system accounts. This helps prevent unauthorized access to systems and data.
- User Education:Educate users about security best practices, such as strong password creation, phishing awareness, and safe browsing habits. This helps prevent future breaches by reducing user vulnerabilities.
Measures Taken to Enhance Security and Prevent Future Breaches
- Vulnerability Management:Implement a robust vulnerability management program to identify and address security vulnerabilities in systems and applications. This involves regularly scanning for vulnerabilities, patching known vulnerabilities, and implementing security controls to mitigate risks.
- Security Awareness Training:Provide security awareness training to all employees to educate them about security best practices, common threats, and how to protect themselves and the organization. This training can help reduce human error and improve security awareness.
- Multi-Factor Authentication:Implement multi-factor authentication for all critical systems and applications. This requires users to provide multiple forms of authentication, such as a password and a one-time code, before they can access systems or data.
- Data Encryption:Encrypt sensitive data at rest and in transit to protect it from unauthorized access. This involves using encryption algorithms to scramble data, making it unreadable to unauthorized individuals.
- Incident Response Plan:Develop and maintain a comprehensive incident response plan that Artikels the steps to be taken in the event of a data breach. This plan should include procedures for identifying the breach, containing the damage, investigating the incident, and recovering from the breach.
- Regular Security Audits:Conduct regular security audits to assess the effectiveness of security controls and identify any weaknesses or vulnerabilities. This helps ensure that security measures are up-to-date and effective in protecting the organization from threats.
Table Outlining Key Remediation Activities and Timelines
| Remediation Activity | Expected Timeline |
|---|---|
| System Recovery | 24-72 hours |
| Data Recovery | 48-168 hours |
| Vulnerability Patching | 24-48 hours |
| Password Reset | 24-48 hours |
| Security Awareness Training | 1-2 weeks |
| Incident Response Plan Review | 1-2 weeks |
End of Discussion
Navigating a data breach is a complex and multifaceted process that demands a strategic approach. By understanding the timeline of events from initial breach detection to settlement payout, organizations can equip themselves with the knowledge and resources to respond effectively, mitigate damage, and protect their stakeholders.
The process emphasizes collaboration, transparency, and a commitment to data security best practices.
FAQs
What are the common types of data breaches?
Discover the crucial elements that make Capital One Settlement Case Timeline the top choice.
Common data breaches include phishing attacks, malware infections, insider threats, and accidental data leaks.
How long does it typically take to reach a settlement after a data breach?
The time it takes to reach a settlement varies depending on the complexity of the breach, the number of affected individuals, and the legal framework involved. It can range from several months to several years.
What are some examples of settlement payouts in data breach cases?
Settlement payouts can include financial compensation for affected individuals, credit monitoring services, identity theft protection, and legal fees.