The Capital One Data Breach: What Happened? In 2019, a massive data breach shook the financial services industry, affecting millions of individuals. This incident, orchestrated by a skilled hacker, exposed sensitive personal and financial information, raising concerns about data security and privacy.
This article delves into the details of the breach, examining the timeline of events, the scope of the compromised data, the hacker’s methods, and Capital One’s response.
Remember to click How to Understand the Legalese in the Settlement to understand more comprehensive aspects of the How to Understand the Legalese in the Settlement topic.
The breach, which was discovered in July 2019, involved the theft of data from Capital One’s systems. The hacker, Paige Thompson, exploited a misconfigured web application firewall to gain unauthorized access. The stolen data included names, addresses, social security numbers, credit card numbers, and bank account details.
You also will receive the benefits of visiting Capital One Data Breach Overview today.
The impact on affected individuals was significant, with potential risks of identity theft, financial fraud, and reputational damage.
Contents List
The Capital One Data Breach: What Happened?
In July 2019, Capital One, a major financial institution, experienced a significant data breach that impacted millions of individuals. This incident highlighted the vulnerabilities of even large and well-established organizations to cyberattacks and raised serious concerns about data security and privacy.
In this topic, you find that Understanding the Settlement: Legal FAQs is very useful.
This article will delve into the details of the Capital One data breach, examining the timeline of events, the scope of the breach, the hacker’s methods, Capital One’s response, and the lessons learned from this incident.
Timeline of Events
The Capital One data breach unfolded over a period of several months, beginning with the initial intrusion and culminating in the discovery and containment of the breach. Here is a chronological breakdown of key events:
- March 2019:The hacker, Paige Thompson, gained unauthorized access to Capital One’s systems.
- July 17, 2019:Capital One discovered the breach and began investigating the incident.
- July 19, 2019:Capital One contacted law enforcement authorities to report the breach.
- July 22, 2019:Capital One publicly disclosed the breach and began notifying affected individuals.
- July 23, 2019:Thompson was arrested by the FBI.
The Scope of the Breach, The Capital One Data Breach: What Happened?
The Capital One data breach affected a significant number of individuals, compromising sensitive personal and financial information. The scope of the breach was substantial, impacting millions of customers.
- 100 million individuals:The breach affected approximately 100 million individuals who had applied for a Capital One credit card or bank account between 2005 and 2019.
- Data compromised:The data compromised included names, addresses, social security numbers, credit card numbers, bank account details, dates of birth, and other sensitive information.
- Potential impact:The breach had the potential to lead to identity theft, fraud, and other financial crimes. Affected individuals faced the risk of unauthorized access to their personal and financial information, potentially leading to financial losses and reputational damage.
The Hacker and Their Methods
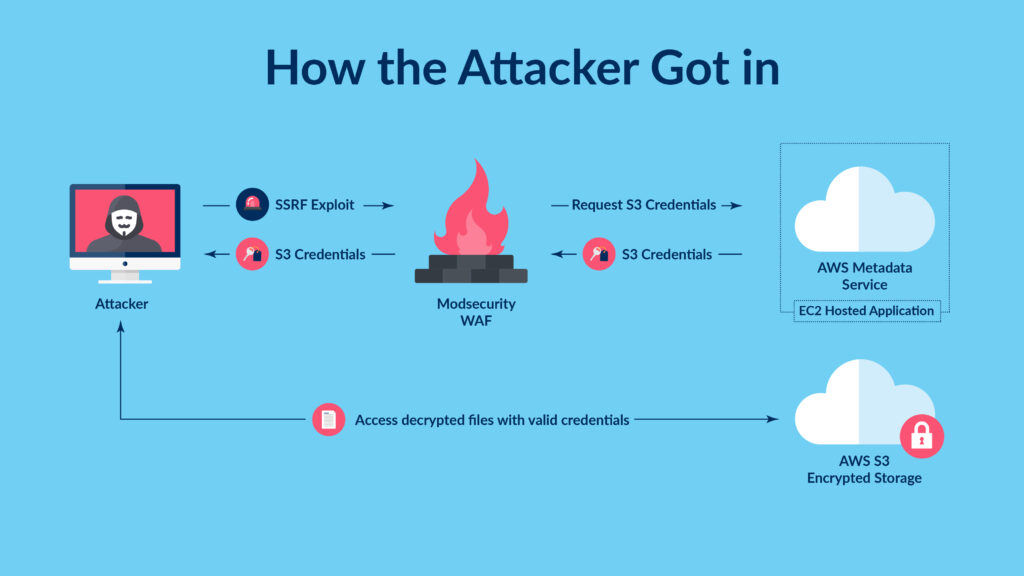
The hacker responsible for the Capital One data breach was Paige Thompson, a former Amazon Web Services (AWS) employee. Thompson exploited a misconfigured web application firewall (WAF) to gain access to Capital One’s systems. The WAF was designed to protect against malicious attacks, but Thompson was able to bypass its security measures.
Find out further about the benefits of How Lawyers Reached the Capital One Settlement Agreement that can provide significant benefits.
- Exploiting a misconfigured WAF:Thompson exploited a vulnerability in the WAF, which was improperly configured and allowed unauthorized access to Capital One’s systems.
- Using AWS credentials:Thompson used stolen AWS credentials to access Capital One’s data. These credentials were likely obtained through a separate breach or through other illicit means.
- Data exfiltration:Thompson downloaded a large amount of data from Capital One’s systems, including sensitive personal and financial information.
Capital One’s Response
Capital One took a number of steps to address the breach, including notifying affected individuals, implementing security measures, and offering credit monitoring and identity theft protection services.
Get the entire information you require about Understanding the Legal Terms in the Capital One Settlement on this page.
- Notification of affected individuals:Capital One sent letters and emails to affected individuals, informing them of the breach and providing information on steps they could take to protect themselves.
- Implementation of security measures:Capital One implemented enhanced security measures to prevent future breaches, including strengthening its WAF and improving its data security practices.
- Credit monitoring and identity theft protection:Capital One offered affected individuals free credit monitoring and identity theft protection services to help mitigate the potential risks associated with the breach.
Lessons Learned
The Capital One data breach serves as a stark reminder of the importance of data security and privacy. It highlights the need for organizations to invest in robust security measures and to be vigilant in protecting sensitive information.
Browse the implementation of Capital One Data Breach and Legal Precedents in real-world situations to understand its applications.
- Importance of data security:The breach emphasizes the critical need for organizations to prioritize data security and implement comprehensive measures to protect sensitive information.
- Vulnerability of cloud-based systems:The breach highlights the vulnerabilities of cloud-based systems, particularly those that rely on third-party services.
- Importance of employee training:The breach underscores the importance of employee training and awareness regarding data security best practices.
Impact on the Industry
The Capital One data breach had a significant impact on the financial services industry, prompting a renewed focus on data security and privacy. It also led to increased scrutiny of data security regulations and best practices.
Further details about Legal Ramifications of the Capital One Breach is accessible to provide you additional insights.
- Increased scrutiny of data security:The breach led to increased scrutiny of data security practices within the financial services industry, with regulators and lawmakers calling for enhanced security measures.
- Data security regulations:The breach prompted a review of data security regulations, with a focus on strengthening requirements for data protection and breach notification.
- Evolving landscape of cybersecurity threats:The breach highlights the evolving nature of cybersecurity threats, with hackers constantly developing new techniques to exploit vulnerabilities.
Last Point
The Capital One data breach serves as a stark reminder of the ever-present threat of cyberattacks. The incident highlighted the importance of robust security measures, comprehensive data protection practices, and a proactive approach to cybersecurity. Organizations must prioritize data security and privacy, investing in advanced technologies and training to mitigate risks.
The financial services industry, in particular, needs to adapt to the evolving landscape of cybersecurity threats, implementing stringent security protocols and fostering a culture of vigilance.
In this topic, you find that What Happens When a Company Settles a Data Breach? is very useful.
Commonly Asked Questions
What was the hacker’s motive?
The hacker, Paige Thompson, initially claimed to have stolen the data for personal gain. However, she later stated that her intention was to expose vulnerabilities in Capital One’s security systems.
Enhance your insight with the methods and methods of What Is a Class Action Settlement?.
What steps did Capital One take to prevent future breaches?
Discover how The Class Action Lawsuit Against Capital One has transformed methods in this topic.
Capital One implemented a number of security measures, including enhanced monitoring, vulnerability assessments, and employee training. They also worked with law enforcement to investigate the breach and prosecute the hacker.
Understand how the union of Class Action Settlements: What You Need to Know can improve efficiency and productivity.
How can I protect myself from data breaches?
You can protect yourself by using strong passwords, enabling two-factor authentication, and monitoring your credit reports regularly. You should also be cautious about sharing personal information online and be aware of phishing scams.