Will Capital One’s Security Hold Up in the Future? sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. Capital One, a prominent financial institution, has faced its share of security challenges, leaving many questioning its ability to withstand future threats.
This exploration delves into Capital One’s security history, dissecting past breaches and analyzing the company’s response to them. It examines the current security measures in place and assesses their effectiveness in protecting customer data. Moreover, it addresses the evolving landscape of cyber threats, highlighting the specific challenges Capital One faces in adapting to these emerging dangers.
Browse the implementation of Long-Term Impact of the Settlement on Capital One in real-world situations to understand its applications.
Ultimately, the discussion examines potential future security strategies, emphasizing the importance of industry best practices and the need to rebuild customer trust.
This examination provides a comprehensive overview of Capital One’s security landscape, considering its past, present, and future. It explores the company’s security history, analyzes its current security posture, and investigates potential future threats. By evaluating Capital One’s security practices against industry best practices, the discussion sheds light on areas where the company can improve its security posture.
The article emphasizes the critical role of customer trust in maintaining a secure financial environment and explores strategies for rebuilding trust after breaches. The analysis ultimately provides a roadmap for Capital One to strengthen its security measures and ensure the protection of its customers’ data.
Contents List
Capital One’s Security History
Capital One, a prominent financial institution, has a history of experiencing significant security breaches. These incidents have raised concerns about the company’s ability to safeguard customer data and have impacted its reputation and customer trust. Understanding the history of these breaches is crucial to assess Capital One’s current security measures and anticipate potential vulnerabilities in the future.
Major Security Breaches
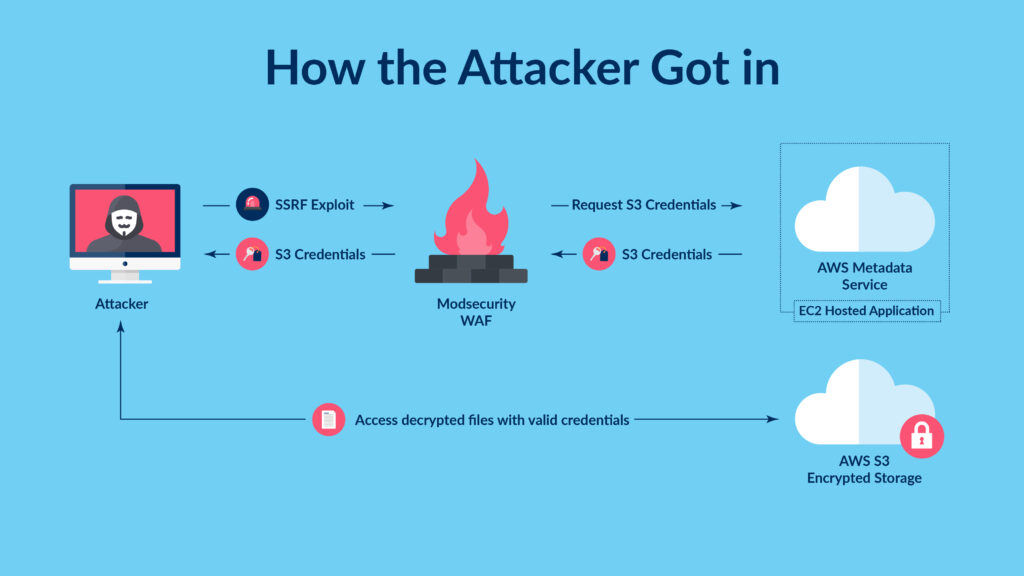
- 2019 Data Breach:In 2019, Capital One suffered a major data breach that compromised the personal information of over 100 million customers. The breach was attributed to a misconfigured web application firewall that allowed an attacker to access sensitive data, including Social Security numbers, credit card numbers, and bank account details.
The impact of this breach was significant, leading to a loss of customer trust and a $80 million settlement with the Federal Trade Commission.
- 2017 Data Breach:In 2017, Capital One experienced a smaller data breach affecting approximately 1 million customers. The breach involved the theft of credit card numbers and other sensitive information. This incident highlighted the vulnerability of Capital One’s systems to unauthorized access and the need for stronger security measures.
Impact on Reputation and Customer Trust
The 2019 data breach significantly damaged Capital One’s reputation and eroded customer trust. The company faced public scrutiny and criticism for its security practices. The breach also led to a decline in customer satisfaction and increased concerns about the safety of personal information.
Explore the different advantages of What Will Happen to Capital One’s Reputation? that can change the way you view this issue.
To regain customer trust, Capital One implemented several initiatives, including providing credit monitoring and identity theft protection services to affected customers. The company also invested in enhanced security measures and increased transparency regarding its security practices.
Vulnerabilities Exploited
The vulnerabilities exploited in Capital One’s data breaches have varied but often involved common security flaws, such as misconfigured web application firewalls, outdated software, and weak access controls. In the 2019 breach, the attacker exploited a misconfigured web application firewall to gain access to sensitive data.
This incident highlighted the importance of proper configuration and maintenance of security systems to prevent unauthorized access.
Check Capital One’s Commitment to Security Post-Settlement to inspect complete evaluations and testimonials from users.
Mitigation and Security Improvements
Following each security breach, Capital One has taken steps to mitigate the impact and improve its security posture. These measures have included:
- Enhanced Security Infrastructure:Capital One has invested in advanced security technologies, including intrusion detection and prevention systems, firewalls, and data encryption. These technologies help to protect sensitive data from unauthorized access and cyberattacks.
- Improved Security Practices:The company has implemented stricter security policies and procedures, including enhanced access controls, data encryption, and regular security audits. These measures aim to minimize the risk of data breaches and ensure the confidentiality, integrity, and availability of customer information.
- Increased Transparency:Capital One has made efforts to be more transparent with customers about its security practices and the steps it takes to protect their data. The company has also provided more information about data breaches and the actions it takes to mitigate the impact.
Current Security Measures
Capital One has implemented various security measures to protect customer data and mitigate the risk of future breaches. These measures include advanced technologies, rigorous security practices, and ongoing security assessments.
Investigate the pros of accepting Will Capital One Face More Legal Issues? in your business strategies.
Security Infrastructure and Technologies
- Data Encryption:Capital One uses encryption to protect sensitive customer data both in transit and at rest. This means that data is scrambled and unreadable to unauthorized individuals. Encryption is a fundamental security measure that helps to prevent data breaches and ensure the confidentiality of sensitive information.
- Intrusion Detection and Prevention Systems:Capital One employs intrusion detection and prevention systems to monitor network traffic and identify suspicious activity. These systems help to detect and prevent unauthorized access to sensitive data and systems. Intrusion detection systems alert security personnel to potential threats, while intrusion prevention systems block malicious traffic from entering the network.
- Firewalls:Capital One uses firewalls to control network traffic and prevent unauthorized access to its systems. Firewalls act as a barrier between the company’s internal network and the external internet, blocking malicious traffic and protecting sensitive data from unauthorized access.
- Multi-Factor Authentication:Capital One uses multi-factor authentication (MFA) to enhance the security of customer accounts. MFA requires users to provide multiple forms of authentication, such as a password and a one-time code sent to their mobile device. This helps to prevent unauthorized access even if a password is compromised.
Security Practices and Policies
- Regular Security Audits:Capital One conducts regular security audits to identify and address potential vulnerabilities in its systems and applications. These audits involve scanning for security flaws, testing security controls, and assessing the overall security posture of the company’s infrastructure.
- Employee Training:Capital One provides regular security awareness training to employees to educate them about security threats, best practices, and the importance of data protection. This training helps to reduce the risk of human error and improve the overall security culture within the company.
- Data Loss Prevention (DLP):Capital One uses data loss prevention (DLP) technologies to prevent sensitive data from leaving the company’s network without authorization. DLP solutions monitor network traffic and data transfers to identify and block attempts to transfer sensitive information to unauthorized destinations.
Effectiveness of Security Measures
Capital One’s current security measures have been effective in reducing the risk of data breaches and protecting customer data. The company’s investment in advanced technologies, rigorous security practices, and ongoing security assessments has helped to improve its security posture. However, it is important to note that the cybersecurity landscape is constantly evolving, and new threats emerge regularly.
Capital One must continue to adapt its security measures to address these emerging threats and maintain a strong security posture.
Potential Weaknesses and Vulnerabilities
Despite its investments in security, Capital One’s security approach still faces potential weaknesses and vulnerabilities. These include:
- Third-Party Risk:Capital One relies on third-party vendors for various services, such as data processing and cloud computing. These vendors may have their own security vulnerabilities, which could expose Capital One’s data to risk. The company must carefully vet and monitor its third-party vendors to ensure they meet its security standards.
- Social Engineering:Social engineering attacks, such as phishing emails and phone calls, can trick employees into revealing sensitive information or granting unauthorized access to systems. Capital One must continue to educate its employees about social engineering tactics and implement security measures to protect against these attacks.
- Emerging Technologies:The rapid adoption of new technologies, such as artificial intelligence (AI) and cloud computing, presents new security challenges. Capital One must adapt its security measures to address the unique vulnerabilities associated with these technologies. For example, AI systems can be vulnerable to adversarial attacks, and cloud computing environments require robust security controls to protect data and applications.
Emerging Threats and Challenges
The cybersecurity landscape is constantly evolving, with new threats and vulnerabilities emerging regularly. Capital One must stay ahead of these threats and adapt its security measures to address the changing landscape. This section explores the evolving landscape of cyber threats, the impact of new technologies on security, and the specific threats that pose the greatest risk to Capital One.
Evolving Landscape of Cyber Threats
Cybercriminals are constantly developing new techniques and exploiting emerging vulnerabilities. Some of the most significant emerging threats include:
- Ransomware Attacks:Ransomware attacks have become increasingly common, with attackers encrypting data and demanding payment for its release. These attacks can disrupt operations, damage reputation, and result in significant financial losses. Capital One must implement robust security measures to prevent ransomware attacks, including regular backups, strong endpoint security, and employee training.
Further details about Capital One’s Financial Future After the Settlement is accessible to provide you additional insights.
- Advanced Persistent Threats (APTs):APTs are sophisticated cyberattacks that target specific organizations, often with the goal of stealing sensitive data or disrupting operations. These attacks can be difficult to detect and defend against, requiring advanced security technologies and proactive threat intelligence.
- Zero-Day Exploits:Zero-day exploits target vulnerabilities that are unknown to vendors and have not yet been patched. These exploits can be highly effective and difficult to defend against. Capital One must maintain a strong patch management program and stay informed about emerging vulnerabilities to mitigate the risk of zero-day exploits.
Impact of New Technologies on Security
The adoption of new technologies, such as AI and cloud computing, presents both opportunities and challenges for cybersecurity. While these technologies can enhance security capabilities, they also introduce new vulnerabilities that must be addressed.
- Artificial Intelligence (AI):AI can be used to improve security by automating tasks, detecting anomalies, and responding to threats in real time. However, AI systems themselves can be vulnerable to adversarial attacks, where attackers manipulate the AI model to produce incorrect or malicious outputs.
Capital One must carefully assess the security of AI systems and implement safeguards to protect against adversarial attacks.
- Cloud Computing:Cloud computing offers flexibility and scalability, but it also introduces new security challenges. Data stored in the cloud must be protected from unauthorized access, and the cloud provider’s security controls must be robust. Capital One must carefully select cloud providers, ensure the security of data stored in the cloud, and implement strong access controls to protect sensitive information.
Specific Threats to Capital One
Capital One faces specific threats related to its business model and the sensitive data it handles. These threats include:
- Data Breaches:As a financial institution, Capital One is a prime target for data breaches, as attackers seek to steal sensitive financial information, such as credit card numbers and bank account details. The company must continue to invest in advanced security technologies and implement robust security practices to prevent data breaches.
- Fraudulent Activity:Capital One is vulnerable to fraudulent activity, such as unauthorized transactions, identity theft, and account takeovers. The company must implement strong fraud detection and prevention measures, including real-time transaction monitoring, account authentication, and fraud investigation capabilities.
- Regulatory Compliance:Capital One is subject to strict regulatory requirements related to data privacy and security. The company must ensure its security measures comply with these regulations to avoid fines and penalties. This requires ongoing monitoring and assessment of its security posture to ensure compliance with evolving regulations.
Investigate the pros of accepting Capital One’s Response and Security Improvements in your business strategies.
Challenges in Adapting to Emerging Threats, Will Capital One’s Security Hold Up in the Future?
Capital One faces several challenges in adapting to emerging threats, including:
- Rapidly Evolving Threat Landscape:The cybersecurity landscape is constantly changing, with new threats and vulnerabilities emerging regularly. Capital One must stay informed about the latest threats and adapt its security measures accordingly. This requires continuous monitoring, threat intelligence, and a proactive approach to security.
- Talent Acquisition:Finding and retaining skilled cybersecurity professionals is a significant challenge for many organizations, including Capital One. The company must invest in talent development programs and offer competitive salaries and benefits to attract and retain top cybersecurity talent.
- Resource Constraints:Implementing robust cybersecurity measures requires significant financial resources and investment. Capital One must prioritize security investments and allocate resources effectively to address the most critical threats.
Future Security Strategies
To address future threats and maintain a strong security posture, Capital One needs a comprehensive security strategy that incorporates emerging technologies, proactive threat intelligence, and a culture of security. This section Artikels a potential security strategy for Capital One, including key security investments and strategies for leveraging emerging technologies.
Comprehensive Security Strategy
Capital One’s future security strategy should be based on the following principles:
- Proactive Threat Intelligence:Capital One should invest in advanced threat intelligence capabilities to stay informed about emerging threats and vulnerabilities. This includes monitoring threat actor activity, analyzing threat intelligence reports, and sharing information with other organizations. Proactive threat intelligence allows Capital One to anticipate and mitigate threats before they can impact the company.
- Zero Trust Security:Capital One should adopt a zero trust security model, which assumes that no user or device can be trusted by default. This model requires strong authentication, authorization, and continuous monitoring to verify the identity and integrity of users and devices.
Zero trust security helps to prevent unauthorized access and data breaches by limiting access to sensitive data and systems.
- Security Automation:Capital One should automate security tasks, such as vulnerability scanning, patch management, and incident response. Automation reduces the risk of human error and improves the efficiency of security operations. This allows security teams to focus on more strategic tasks, such as threat intelligence and incident analysis.
Investigate the pros of accepting Capital One’s Post-Settlement Strategy in your business strategies.
- Security Awareness Training:Capital One should continue to invest in security awareness training for employees, covering topics such as social engineering, phishing attacks, and data security best practices. This training helps to reduce the risk of human error and improve the overall security culture within the company.
- Security Culture:Capital One should foster a culture of security, where all employees are responsible for protecting sensitive data and systems. This includes promoting security awareness, encouraging employees to report suspicious activity, and rewarding security excellence.
Key Security Investments
Capital One should prioritize the following security investments:
| Investment Area | Description | Benefits |
|---|---|---|
| Advanced Threat Intelligence | Investing in threat intelligence platforms and services to stay informed about emerging threats and vulnerabilities. | Improved threat detection and prevention, proactive security measures, reduced risk of attacks. |
| Zero Trust Security | Implementing a zero trust security model, which assumes that no user or device can be trusted by default. | Enhanced security posture, reduced risk of unauthorized access, improved data protection. |
| Security Automation | Automating security tasks, such as vulnerability scanning, patch management, and incident response. | Improved efficiency of security operations, reduced risk of human error, faster response to threats. |
| Security Awareness Training | Providing ongoing security awareness training to employees, covering topics such as social engineering, phishing attacks, and data security best practices. | Reduced risk of human error, improved security culture, increased employee awareness of security threats. |
| Emerging Technologies | Investing in emerging technologies, such as AI and blockchain, to enhance security capabilities. | Improved threat detection and prevention, enhanced data protection, increased security resilience. |
Leveraging Emerging Technologies
Capital One can leverage emerging technologies to enhance its security posture, including:
- Artificial Intelligence (AI):AI can be used to automate security tasks, detect anomalies, and respond to threats in real time. Capital One can use AI to improve threat intelligence, analyze security data, and detect suspicious activity. However, it is crucial to ensure the security of AI systems themselves to prevent adversarial attacks.
Find out about how What’s Next for Capital One After the Settlement? can deliver the best answers for your issues.
- Blockchain:Blockchain technology can enhance data security and integrity by providing a tamper-proof record of transactions. Capital One can use blockchain to secure sensitive data, such as customer records and financial transactions, and to improve the transparency and accountability of its security processes.
Find out about how How Capital One Plans to Rebuild Trust can deliver the best answers for your issues.
- Quantum Computing:Quantum computing has the potential to revolutionize cybersecurity by enabling faster and more powerful encryption algorithms. Capital One should explore the potential of quantum computing to enhance its security posture and protect against future threats. However, it is important to note that quantum computing also poses new security challenges, such as the ability to break existing encryption algorithms.
Capital One must invest in research and development to address these challenges and prepare for the future of cybersecurity.
Building a Resilient and Proactive Security Posture
Capital One can build a more resilient and proactive security posture by:
- Continuous Monitoring:Capital One should implement continuous monitoring of its systems and applications to detect and respond to threats in real time. This includes monitoring network traffic, user activity, and security logs for suspicious activity.
- Incident Response:Capital One should have a well-defined incident response plan to quickly and effectively respond to security incidents. This plan should include steps for containing the incident, mitigating the impact, and recovering from the breach.
- Collaboration and Information Sharing:Capital One should collaborate with other organizations and industry partners to share threat intelligence and best practices. This helps to improve the collective security posture of the industry and reduce the risk of attacks.
Wrap-Up: Will Capital One’s Security Hold Up In The Future?
The future of cybersecurity is a complex and evolving landscape. As technology advances, so do the threats that target it. Capital One, like many other financial institutions, faces the ongoing challenge of safeguarding sensitive customer data. By examining its past, analyzing its present, and planning for the future, Capital One can build a more resilient and proactive security posture.
The company’s commitment to industry best practices, customer trust, and transparency will be crucial in navigating the ever-changing world of cybersecurity. Ultimately, Capital One’s success in securing its systems and protecting its customers’ data will depend on its ability to adapt, innovate, and stay ahead of emerging threats.
FAQ Overview
What are the most common types of cyber threats facing financial institutions like Capital One?
Obtain recommendations related to Can Capital One Recover From the Data Breach? that can assist you today.
Common cyber threats facing financial institutions include phishing attacks, malware infections, data breaches, denial-of-service attacks, and ransomware attacks. These threats can compromise customer data, disrupt operations, and damage reputation.
Further details about How Capital One Is Handling Ongoing Breach Concerns is accessible to provide you additional insights.
How can Capital One improve its communication with customers about security?
Capital One can enhance communication with customers about security by providing clear and concise information about potential threats, security measures in place, and steps customers can take to protect themselves. Regular updates and proactive communication can build trust and confidence.
What role does artificial intelligence (AI) play in cybersecurity?
AI plays a significant role in cybersecurity by automating threat detection, analyzing large datasets for anomalies, and responding to threats in real-time. AI-powered security solutions can help financial institutions like Capital One stay ahead of evolving threats.