Investigating the Capital One Breach: Lessons Learned, the 2019 cyberattack that exposed the personal information of over 100 million individuals, serves as a stark reminder of the vulnerabilities inherent in digital systems. This incident, which involved the theft of sensitive data such as Social Security numbers, credit card information, and bank account details, underscores the need for robust cybersecurity measures in today’s interconnected world.
In this topic, you find that Understanding the Legal Terms in the Capital One Settlement is very useful.
This investigation delves into the details of the attack, exploring the attacker’s methods, the security measures in place, and the crucial lessons learned that can help organizations bolster their defenses against future threats.
Do not overlook explore the latest data about What Happens When a Company Settles a Data Breach?.
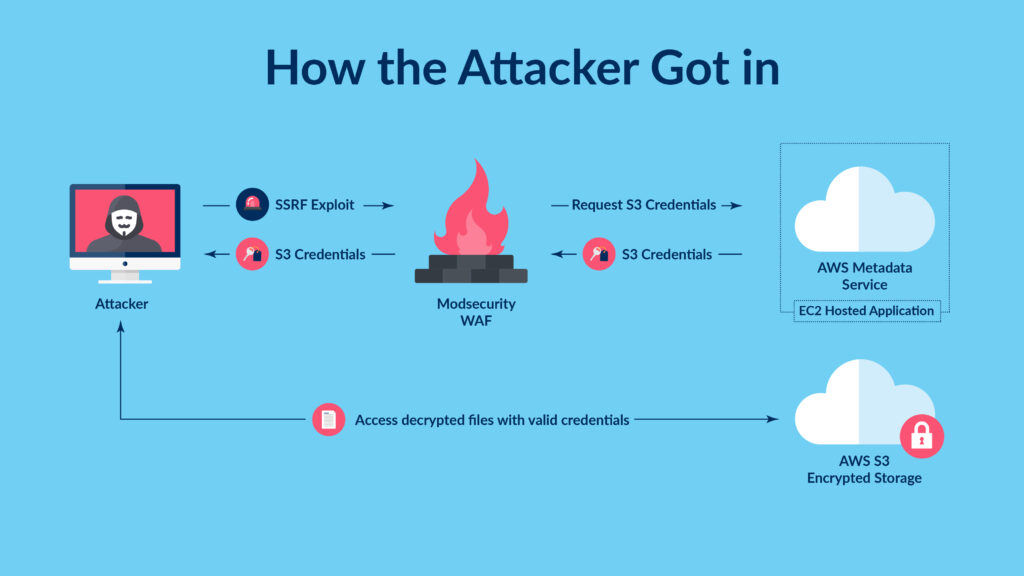
The Capital One breach was a sophisticated attack that exploited a misconfigured firewall to gain access to the company’s systems. The attacker, Paige Thompson, was able to exfiltrate data over a period of several months, highlighting the importance of continuous monitoring and threat detection.
The incident also exposed weaknesses in Capital One’s security posture, prompting the company to implement significant changes to its security practices and invest in advanced security technologies.
In this topic, you find that Capital One Data Breach Overview is very useful.
Contents List
Overview of the Capital One Breach
The Capital One data breach, which occurred in July 2019, was a significant cybersecurity incident that affected millions of individuals. The breach involved the theft of sensitive personal information, including names, addresses, Social Security numbers, credit card numbers, and bank account details.
The incident highlighted the vulnerability of large corporations to cyberattacks and the importance of robust cybersecurity measures.
Scope and Impact of the Breach
The Capital One breach impacted approximately 106 million individuals, making it one of the largest data breaches in history. The attacker, Paige Thompson, a former Amazon Web Services (AWS) employee, exploited a misconfigured firewall to gain access to Capital One’s systems.
Do not overlook explore the latest data about How Lawyers Reached the Capital One Settlement Agreement.
Thompson then used malicious software to exfiltrate data from the company’s cloud storage.
In this topic, you find that How to Understand the Legalese in the Settlement is very useful.
Timeline of Events
- July 2019:Thompson gained unauthorized access to Capital One’s systems and began exfiltrating data.
- July 17, 2019:Capital One discovered the breach and immediately initiated an investigation.
- July 22, 2019:Capital One notified affected individuals about the breach.
- July 22, 2019:Thompson was arrested by the FBI.
- July 23, 2019:Capital One filed a lawsuit against Thompson.
The Attacker’s Methods
Thompson’s attack on Capital One involved a combination of technical skills and exploiting vulnerabilities in the company’s security infrastructure.
Exploiting Vulnerabilities
Thompson exploited a misconfigured firewall that allowed her to access Capital One’s systems. The firewall was responsible for controlling network traffic and blocking unauthorized access, but it was not properly configured, allowing Thompson to bypass security controls.
Using Malicious Software
Once Thompson gained access to Capital One’s systems, she used malicious software, including a custom-built tool called “Chisel,” to exfiltrate data. Chisel allowed Thompson to transfer large amounts of data from Capital One’s servers to her own computer.
Exfiltrating Data

Thompson used various methods to exfiltrate data, including:
- Transferring data over the internet using encrypted connections.
- Storing data in cloud storage services.
- Sharing data with other individuals.
Security Measures in Place
Capital One had several security measures in place prior to the breach, including firewalls, intrusion detection systems, and encryption. However, these measures were not sufficient to prevent Thompson’s attack.
Do not overlook the opportunity to discover more about the subject of The Class Action Lawsuit Against Capital One.
Firewalls
Capital One had firewalls in place to control network traffic and block unauthorized access. However, the firewall that Thompson exploited was misconfigured, allowing her to bypass security controls.
Do not overlook explore the latest data about Legal Ramifications of the Capital One Breach.
Intrusion Detection Systems
Capital One also had intrusion detection systems in place to monitor network traffic for suspicious activity. However, Thompson’s attack was sophisticated and managed to evade detection.
Learn about more about the process of Class Action Settlements: What You Need to Know in the field.
Encryption
Capital One encrypted sensitive data, including credit card numbers and Social Security numbers. However, Thompson was able to access and exfiltrate this data before it was encrypted.
Lessons Learned from the Breach
The Capital One breach provided valuable lessons for organizations about the importance of robust cybersecurity measures and the need to continuously improve security practices.
Best Practices for Securing Sensitive Data
- Regular Security Audits:Organizations should conduct regular security audits to identify and address vulnerabilities.
- Vulnerability Assessments:Organizations should conduct vulnerability assessments to identify and remediate weaknesses in their systems.
- Employee Training:Organizations should provide employees with cybersecurity training to raise awareness of threats and best practices.
- Strong Password Policies:Organizations should enforce strong password policies, including the use of complex passwords and regular password changes.
- Multi-Factor Authentication:Organizations should implement multi-factor authentication to add an extra layer of security to user accounts.
- Data Encryption:Organizations should encrypt sensitive data both at rest and in transit.
- Security Monitoring:Organizations should implement security monitoring tools to detect and respond to suspicious activity.
- Incident Response Plan:Organizations should have a comprehensive incident response plan in place to handle security breaches effectively.
The Aftermath of the Breach
The Capital One breach had a significant impact on the company’s reputation and customer trust. The company faced public scrutiny and criticism for its security practices. However, Capital One took steps to address the breach and restore customer confidence.
Do not overlook explore the latest data about Capital One Data Breach and Legal Precedents.
Impact on Reputation and Customer Trust
The breach damaged Capital One’s reputation and led to a decline in customer trust. Customers were concerned about the security of their personal information and the company’s ability to protect their data.
Steps Taken by Capital One, Investigating the Capital One Breach: Lessons Learned
- Notifying Affected Individuals:Capital One notified affected individuals about the breach and provided information about the types of data compromised.
- Providing Credit Monitoring Services:Capital One offered free credit monitoring and identity theft protection services to affected individuals.
- Implementing Enhanced Security Measures:Capital One implemented enhanced security measures, including strengthening its firewall and improving its security monitoring capabilities.
- Public Apology:Capital One issued a public apology to affected individuals and expressed its commitment to protecting customer data.
Regulatory and Legal Implications: Investigating The Capital One Breach: Lessons Learned
The Capital One breach had significant regulatory and legal implications for the company.
Potential Fines and Penalties
Capital One faced potential fines and penalties from regulatory agencies, including the Federal Trade Commission (FTC) and the Office of the Comptroller of the Currency (OCC), for its failure to protect customer data.
Impact on Data Privacy Laws and Regulations
The breach highlighted the importance of data privacy laws and regulations, such as the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States. The breach led to calls for stronger data privacy protections and increased enforcement of existing regulations.
In this topic, you find that What Is a Class Action Settlement? is very useful.
Ultimate Conclusion
The Capital One breach serves as a critical case study in cybersecurity, offering valuable insights into the evolving landscape of cybercrime and the importance of proactive security measures. The lessons learned from this incident can guide organizations in developing comprehensive security strategies, including the implementation of robust security controls, regular security audits, and employee training programs.
By embracing a culture of security awareness and continuous improvement, organizations can effectively mitigate their risk of falling victim to similar attacks and safeguard the sensitive information entrusted to them.
In this topic, you find that Understanding the Settlement: Legal FAQs is very useful.
FAQ Summary
What was the impact of the Capital One breach on the company’s reputation?
The breach significantly damaged Capital One’s reputation, leading to a decline in customer trust and increased scrutiny from regulators. The company faced public criticism for its security practices and was subject to numerous lawsuits.
What steps did Capital One take to address the breach?
Capital One took several steps to address the breach, including notifying affected individuals, providing credit monitoring services, and implementing enhanced security measures. The company also invested in new technologies to improve its security posture and strengthen its data protection capabilities.
What were the regulatory and legal implications of the Capital One breach?
The Capital One breach resulted in significant regulatory and legal implications. The company faced fines and penalties from regulators, and numerous lawsuits were filed by affected individuals. The breach also highlighted the need for stricter data privacy regulations and increased enforcement of existing laws.